
From speaking to our clients and organisations across many sectors, we know security teams are inundated with a deluge of data and alerts, leading to alert fatigue and diminishing effectiveness in detecting genuine threats.
In a recent study, over 40% of organisations reviewed receive 10,000+ alerts per day and experience a 50% or more rate of false positives. This causes a huge burden of time and money for organisations and platform owners. But fear not, there is a beacon of hope amidst this alerting chaos: Risk-Based Alerting (RBA) available within Splunk ES 7.1.
The Proactive Benefits Of RBA
RBA provides teams with a unique opportunity to pivot cybersecurity resources from reactive to proactive while building out a flexible foundation to mature security operations across multiple departments. As alert fidelity and true positive rates increase, analysts are freed up to work on higher-value tasks, such as threat hunting, adversary simulation, or building up their skill sets.
- Reduction in Alert Volume: With RBA, organisations can experience a significant reduction in alerting volume, up to 50% to 90%. This means fewer alerts to sift through, allowing security teams to focus on high-priority threats.
- Enhanced Detection of Sophisticated Threats: RBA enables the detection of sophisticated threats, including low-and-slow attacks that traditional SIEM solutions often miss. By correlating various data points and leveraging advanced analytics, RBA provides a more comprehensive view of potential security issues.
- Alignment with Cybersecurity Frameworks: RBA seamlessly aligns with established cybersecurity frameworks such as MITRE ATT&CK, Lockheed Martin Cyber Kill Chain, CIS Critical Security Controls, and NIST. This ensures that organisations can adhere to industry best practices and regulatory requirements.
- Increased Analyst Productivity: By reducing the volume of low-fidelity alerts and providing more context for analysis, RBA enhances analyst productivity. This allows security teams to focus on high-value activities such as threat hunting and adversary simulation.
- Smoother Audit Process: RBA helps organisations meet and exceed security audit requirements, resulting in a smoother audit season. By providing higher-fidelity alerts and improved incident response capabilities, RBA ensures that organisations are well-prepared to demonstrate compliance.
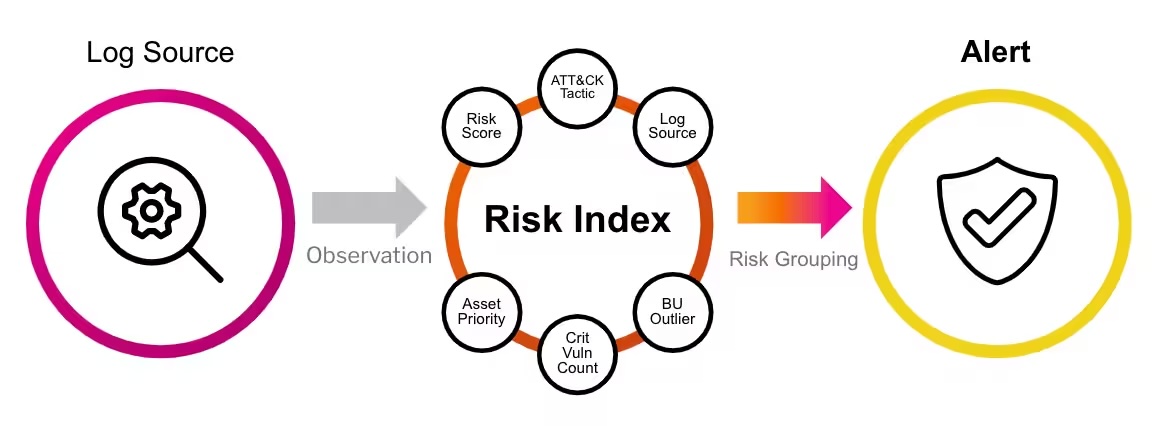
How RBA Works:
RBA leverages Splunk ES’s correlation rule framework to collect and analyze potentially risky events. These events are aggregated into a single Risk Index, where they are evaluated based on predefined criteria. A Risk Notable is generated only when certain criteria warranting an investigation are met, reducing the volume of low-fidelity alerts and providing analysts with more context for analysis.
Traditional vs. Risk-Based Alerting:
In traditional cybersecurity alerting, organisations are inundated with a high volume of alerts, many of which turn out to be false positives. This leads to alert fatigue, slower detection and response times, and an increased risk of missing critical alerts. RBA, on the other hand, focuses on generating higher-fidelity alerts based on the risk level associated with each event. By correlating multiple observations and dynamically adjusting risk scores, RBA provides analysts with a more comprehensive view of potential security issues.
Implementing RBA: Step by Step
Effective implementation of risk-based alerting requires a combination of technology, processes, and expertise. Here are some key steps to consider:
- Define Risk Criteria: Collaborate with stakeholders to define risk criteria based on factors such as asset value, sensitivity of data, and regulatory requirements.
- Integrate Threat Intelligence: Incorporate threat intelligence feeds into the SIEM system to enrich alert data and enhance risk-scoring capabilities.
- Fine-Tune Alerting Rules: Continuously refine alerting rules and thresholds based on real-world feedback and the evolving threat landscape.
- Automate Response Actions: Implement automated response actions for high-risk alerts to minimise manual intervention and accelerate incident response times.
- Training and Awareness: Provide comprehensive training to security teams on interpreting risk-based alerts and responding effectively to security incidents.
The 4 Stages of RBA Methodology
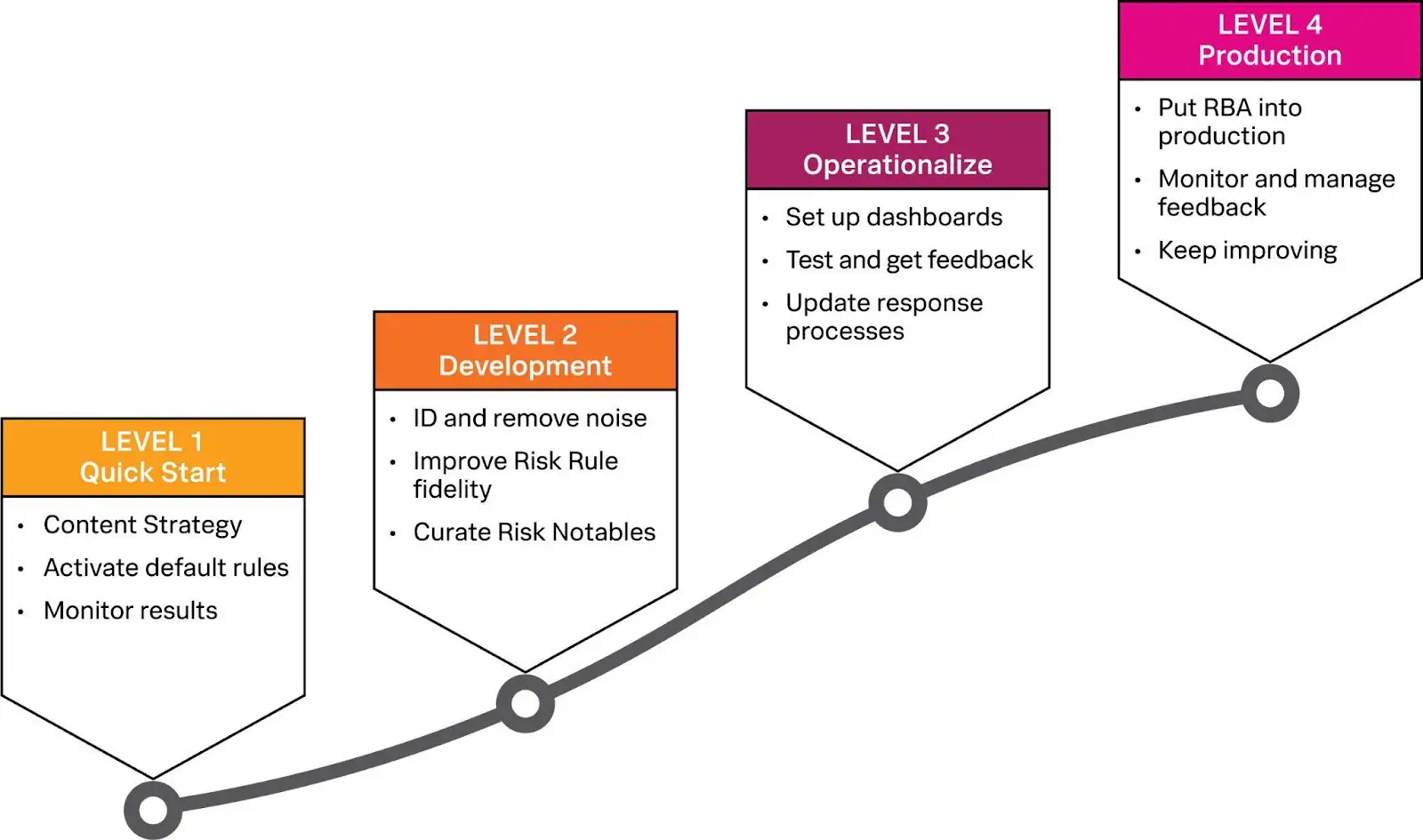
Implementing RBA is an iterative process, requiring organisations to work through four levels of maturity:
- Getting Familiar: Organisations start by familiarising themselves with RBA and monitoring and tuning default rules to produce higher-fidelity alerts.
- Development Phase: This phase involves modifying existing rules to further enhance the quality of Risk Notables.
- Preparing for Production: Organisations prepare their RBA implementation for production by setting up useful dashboards and modifying existing case management processes.
- Going Live: The final phase involves putting RBA into production and carefully monitoring activity and results, fine-tuning rules and processes as needed.
Setting Expectations:
It’s important to set realistic expectations when embarking on an RBA journey. RBA implementation is not a one-time solution but an ongoing process that requires time and resources. However, the benefits of RBA far outweigh the initial investment, with organisations typically experiencing a significant reduction in alerts and improved incident response capabilities.
How long will this RBA journey take? There’s no one answer because every organisation is different: different infrastructure, different resources and different security issues. Some teams will want to do everything on their own; others may choose to engage a Splunk Partner for guidance or to work alongside their internal security team. How many resources you can dedicate to its development and the scope of your implementation also makes a huge difference.
Bringing It All Together and the Next Steps
In conclusion, Risk-Based Alerting represents a big shift in cybersecurity operations, enabling organisations to prioritise their response efforts and stay ahead of emerging threats. By leveraging Splunk’s powerful RBA capability, organisations can streamline their security operations, enhance threat detection capabilities, and mitigate risks more effectively. As organisations continue to face evolving cybersecurity challenges, embracing RBA is essential for staying one step ahead, keeping platforms performing optimally and protecting business interests.
-

24 April 2025
SIEM Migration Trends
-

18 April 2025
Key Differentiators: What an MSSP Will and Won’t Do
-

15 April 2025
The Operating Model
See how we can build your digital capability,
call us on +44(0)845 226 3351 or send us an email…
