Sound Familiar?
Every enterprise needs a SIEM right, for compliance and security?
- SIEM helps me tick the compliance box
- SIEM is slow, cumbersome, my EDR already told me where the problem is
- SIEM, we have it, we ‘operate’ it, I’m struggling with getting value from it
- SIEM is expensive, I’ve bought it, it tells me what it knows, but it’s not very adaptable
- SIEM creates lots of noisy, false positive data, our SOC doesn’t trust it
- SIEM tells our SOC an alert, our SOC tells us the alert, and some triage, it’s not much value
- SIEM is cumbersome to perform analytics upon
- Working only with what the SIEM tells you, versus what you have configured it to tell you based on your contextual data, will invariably fail
If this does sound familiar, apto can jump in at any point in your SIEM journey and help with the above issues.
About apto solutions
Apto bring together, people, platform and process, apto have a proven approach through design, deploy, operate and manage, transfer if desired. The phases and approach, adapt to your required operating model, in-house, hybrid, outsource. We deliver what you require and guide, based on our vast experience, sound good practices and approaches.
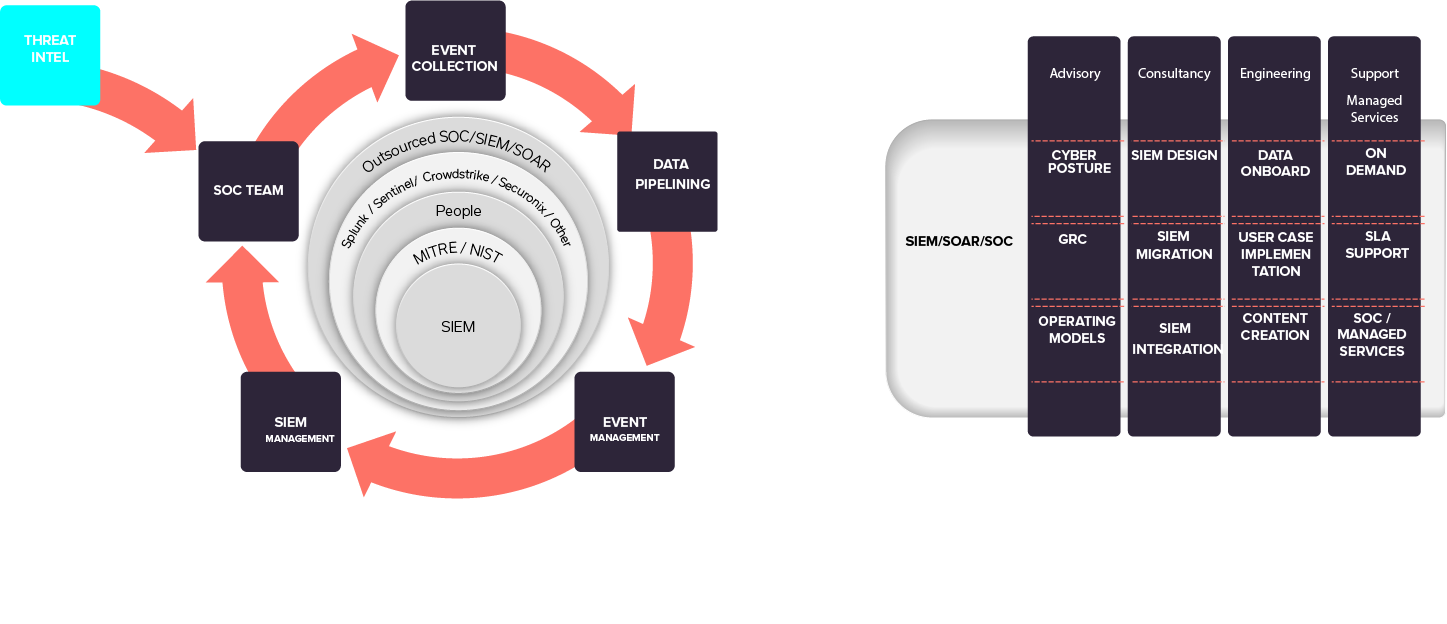
To Consider
Discovery and Planning Phase
- Which policies are important to your business
- Which policies are important for your company’s compliance with rules, and
- Which ones are considered as best practices.
- What policies are required for operation, what for board level reporting and compliance
- How does your SIEM comply with your general risk and compliance policies
- Get your data modelled!
Pilot
Demonstrating the value, a working model and playbooks. What is your return on investment? When you get to the pilot stage, you’re then able to apply lessons learned from the data collected during discovery and implement any improvements you’ve made on a larger subset of policies and devices
Deployment
SIEM does not have to be a big bang rollout. You can gradually and steadily build the uses cases out. During this phase you can validate, prove and improve, and prioritise the use cases. Its good practice, minimises data overload, false positives, and an overall negative impression of a SIEM (we don’t believe anything it tells us, as its alerting non-stop)
Continuous Improvement
It’s not a one off all my uses cases are done thank you; new threats are exponentially increasing, week-on-week, day-by-day. You must protect against this and continue to create and manage your content, a continuous feedback loop with your security operations centre.
There is also tuning and tweaking, additional data onboarding. apto offer a complete, design, implement, operate and transfer service. This is discussed at the onset of any engagement in your preferred method of operation, self sufficient, a program to get there, hybrid, or outsource.
Abiding Principles
- How to prepare and store your data – think data modelling, metadata, classic ETL thinking
- How to give your operation authority and clarity with a solid logging policy
- What metadata is and why you should care about it
- How to develop and structure incident detection logic into your own playbook
- How to continually maintain and create content in your SIEM based on SOC monitoring and feedback
- How do you manage and source threat intel?
- What’s the Total Operations model – in-house, outsource, hybrid
Always what apto will provide to our customers is the principle of abidance !
See how we can build your digital capability,
call us on +44(0)845 226 3351 or send us an email…
-

26 June 2025
SIEM Platform Management
-

26 June 2025
Using Your Data Effectively in Enterprise Security
-

26 June 2025
Data Discovery Process
