Migrate to Sentinel from Legacy SIEM with Apto’s Expert Support
Are you using a legacy SIEM that is no longer meeting your security requirements? It’s time to migrate to Sentinel, a modern, cloud-native SIEM solution from Microsoft, with apto Sentinel Migration. But how do you ensure a smooth and seamless transition without losing any critical data or capabilities ?(its a process that requires lots of thought) That’s where Apto comes in.
Our experienced consultants will conduct a comprehensive assessment of your existing SIEM environment, including your data sources, detection solutions, automation, and reporting. Based on this assessment, we’ll work with you to decide which capabilities and data sets need to be migrated to Sentinel.
We’ll then design and deploy your historic capabilities and data into the new Sentinel instance, setting up ingestion solutions for your existing data sources, creating detective use cases based on your existing detection logic, and replicating and improving your reporting solutions.
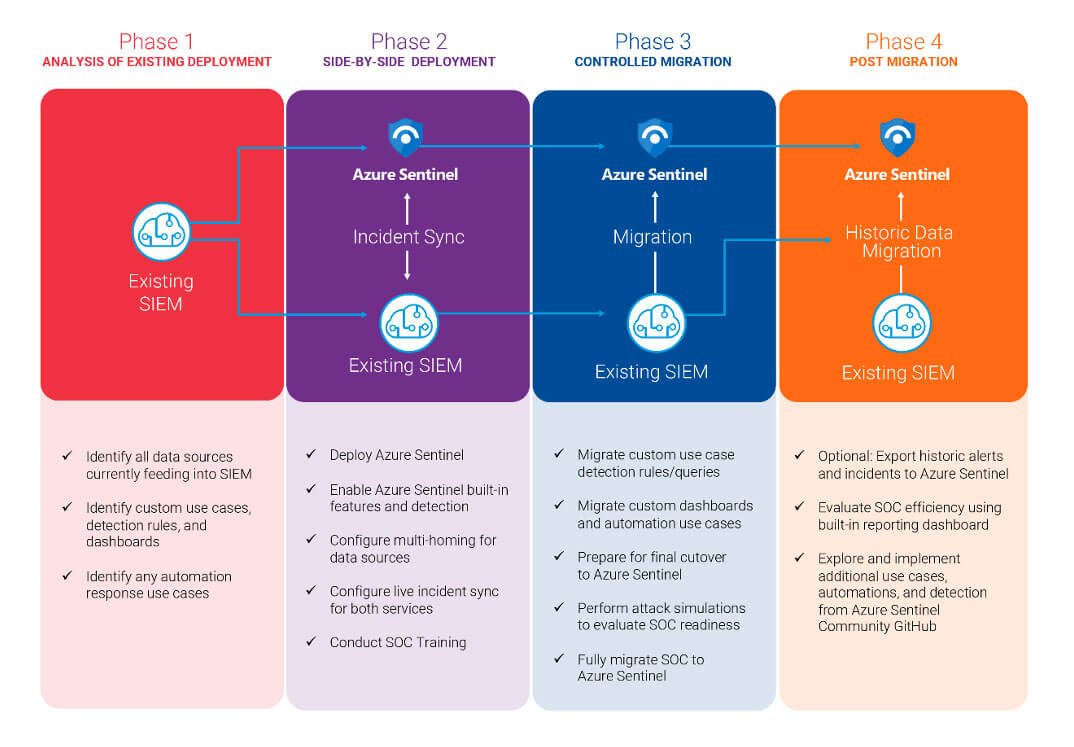
At Apto, we follow a proven SIEM lifecycle methodology that ensures a successful migration to Sentinel. Our approach is based on years of experience and best practices, and we’ll work closely with you every step of the way to ensure your migration process will be smooth and hassle-free.
Discover Phase:
- Identify and Document SOC Processes:
- Document existing SOC processes, including ITSM or third-party tooling integration.
- Assess Data Sources and Risks:
- Review and inventory existing data sources, including asset management solutions.
- Assess existing risks, threats, and data sources for input into detective controls, automation, and reporting.
- Inventory and Review:
- Review and document existing detective use cases, solutions, automation (SOAR), dashboards, and reports.
- Update inventories post-review (data sources, risks, detective use cases, dashboards, automation).
- Migration Specification:
- Produce an overall migration specification and project plan, agreed with the customer.
- Design SOC Processes:
- Confirm the opportunity to design SOC processes maximising Sentinel’s features and integrating with third-party tooling.
Design Phase:
- Security Product Design:
- Design security products and SIEM interaction, integrating with ITSM or third-party tooling.
- SIEM Architecture and Cost Model:
- Develop SIEM architecture for Sentinel, including data pipeline, logging/retention, and data ingestion.
- Create a cost model for the proposed SIEM implementation.
- Data Model and RBAC Design:
- Create a data model for all data sources, including entity mapping/use.
- Design RBAC model and permissions for Sentinel and existing environment workloads.
- Analytics and SOAR Design:
- Design analytics against migration rules.
- Design SOAR actions for migration via Sentinel playbook automation.
- Workbook Factory and Testing:
- Produce specifications and mock-up designs for migrating existing dashboards/reports into workbook format.
- Design end-to-end test scenarios evaluating the SIEM lifecycle.
Deploy Phase:
- Sentinel Instance Deployment:
- Deploy Sentinel instance architecture with logging and data pipeline solutions.
- Data Management and Migration:
- Deploy data source collection solution from required sources.
- Migrate historic data to logging solution and activate retention solution.
- Rule and Solution Deployment:
- Deploy analytics and threat hunting rules, along with supporting automation.
- Deploy automation solutions integrating with ITSM and third-party tooling.
- RBAC Implementation and Workbook Deployment:
- Apply RBAC to the Sentinel instance environment.
- Deploy workbooks and validate against data sets.
- End-to-End Testing:
- Complete end-to-end test scenarios to validate SIEM lifecycle.
Operate Phase:
- Documentation and Review:
- Document operating processes, RACI, and technical reference materials.
- Review and sign-off delivered documentation with the customer.
- Environment Run or Apto Managed Service:
- Run the environment in transition to customer SIEM/SOAR operations team.
- Start Apto managed service for operations and/or content management.
- Monitoring and Optimisation:
- Monitor health of data ingestion solutions and data curation pipeline.
- Validate operating cost, analytics rules, and automation efficacy.
- Optimise as required.
- Validation of Integration and Workbooks:
- Validate ITSM and third-party integration.
- Validate workbooks against ingested data and update as required.
- SOC Process Efficiency Validation:
- Validate SOC process efficiency against Sentinel operation.
- Iterate/improve processes as required.
About Apto Solutions
Our goal is to assist organisations in adopting threat detection platforms which provide a responsive, secure and measurable oversight of sensitive data and critical processes. With extensive experience in Sentinel and relevant certifications in cloud security best practices, cloud services, and architectures on Azure, AWS, GCP, and M365/XDR, we are fully equipped to ensure the safety and security of your data. Trust us to provide top-notch service and peace of mind.
See how we can build your digital capability,
call us on +44(0)845 226 3351 or send us an email…